Oracle Fusion Security Console:
The Oracle Fusion Applications Security Console is an easy-to-use administrative work area where you perform most security-management tasks. This topic introduces the Security Console and describes how to access it
-
Security Console Functions:
Navigation to access Security Console is as below:
Tools—> Security Console
Click on Security Console
Security Console consists of different sections. Each section is having different purpose.
Before going deep into the security concept of Oracle Fusion application, let us create sample test login user.
(2) How to Create Login User in Oracle Fusion:
Navigation: Under security console, click on Users.
Click on Add User Account
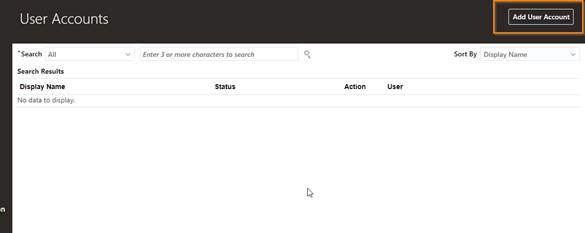
Enter the required user information as shown below:
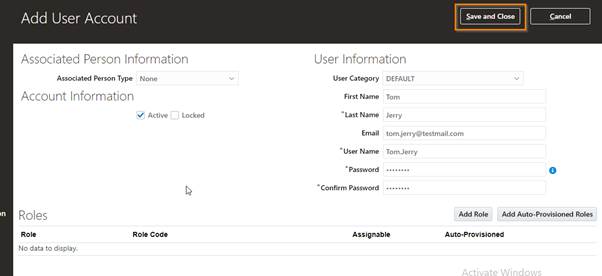
Here we have two important fields:
(A) Associated Person Type:
This field is used when we want to assign user to employee or person created in Oracle Fusion. This will require when we need to give employee specific access to user. For example, Purchase order creation for Buyer.
(B) User Categories:
User category provides you with an option to group set of users such that the specified setting applies to everyone in that group.
We will see this user categories in details in next section.
Click on Save and Close.
Search the new user which is created now.
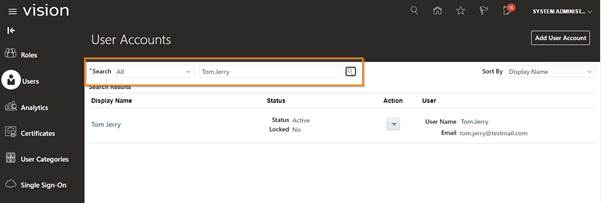
Log in with new User created with Username and Password.

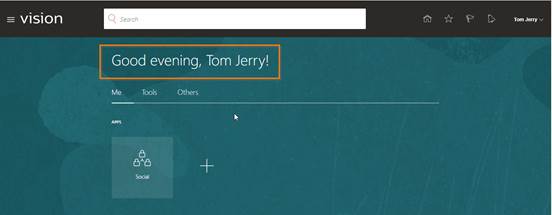
In this way, we can create new user in oracle Cloud ERP instance.
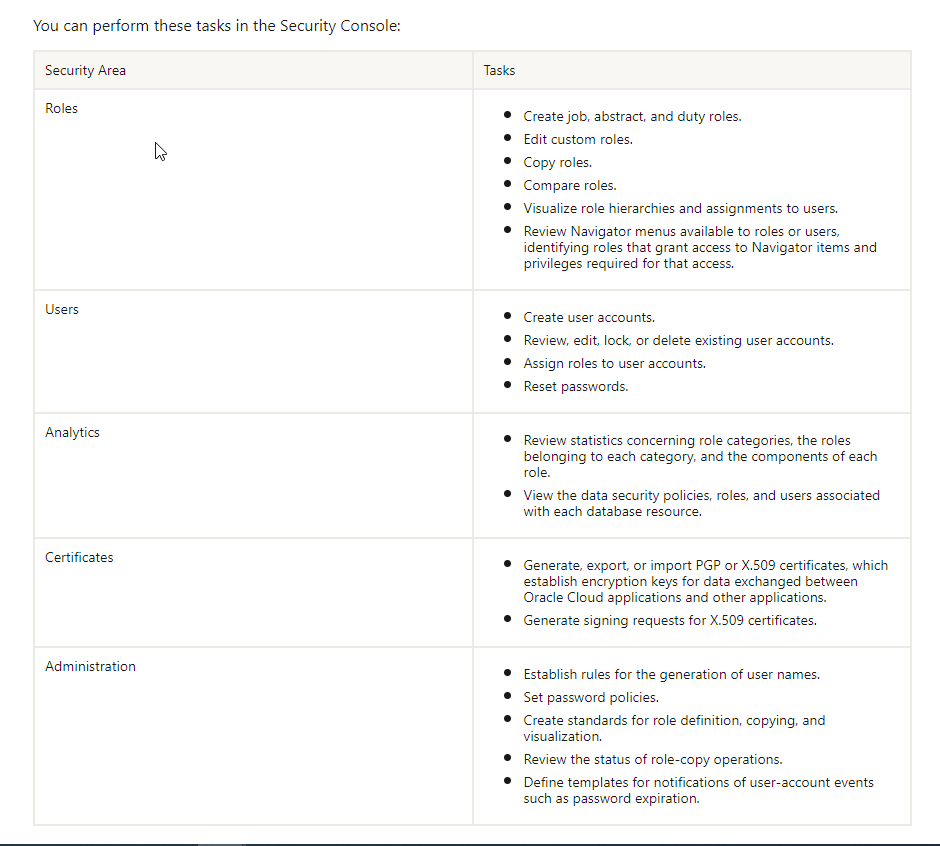
(3) Analytics:
Under Analytics section of security console, we can review statistics concerning role categories, roles belonging to each category and components of each role.
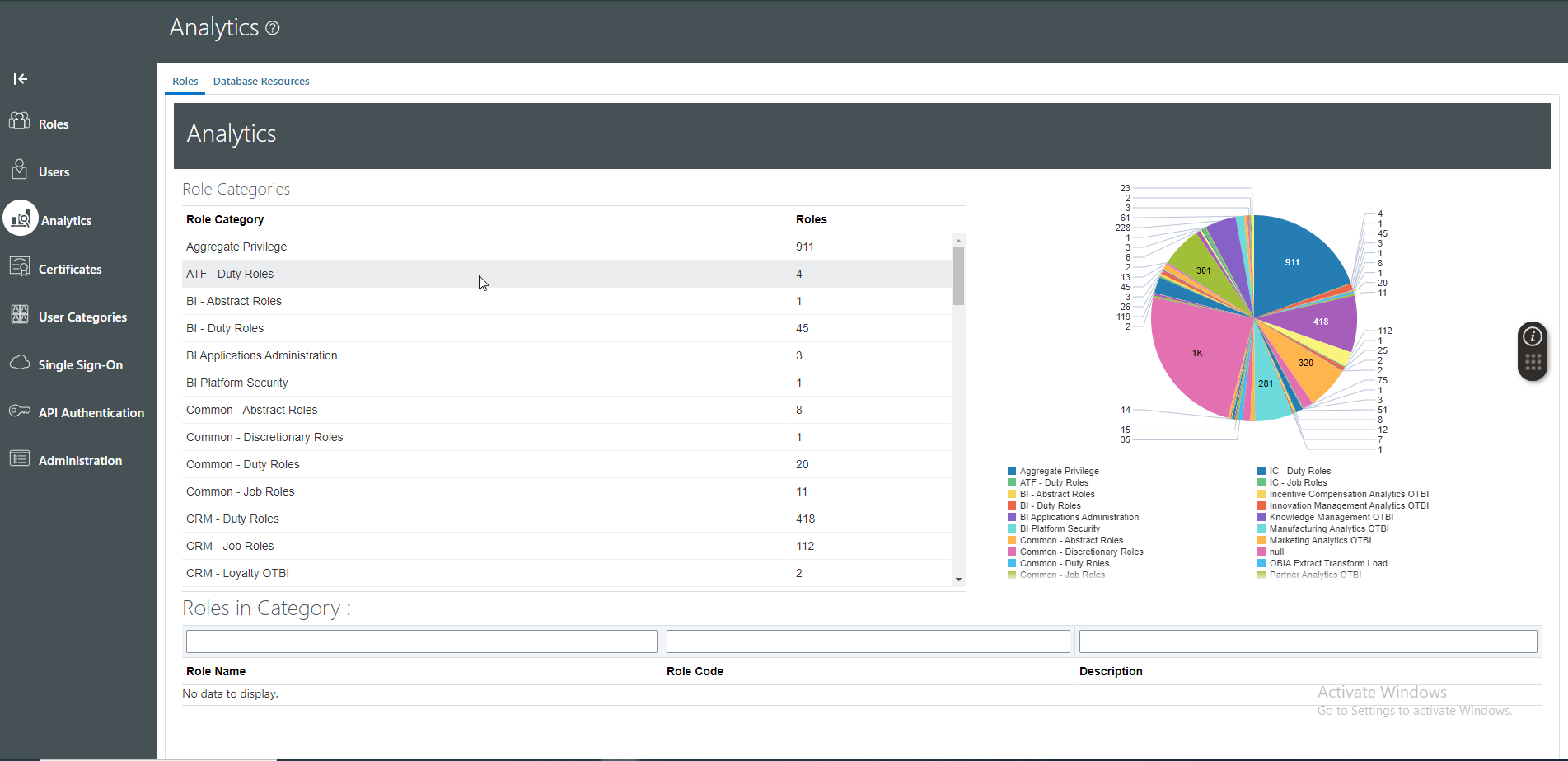
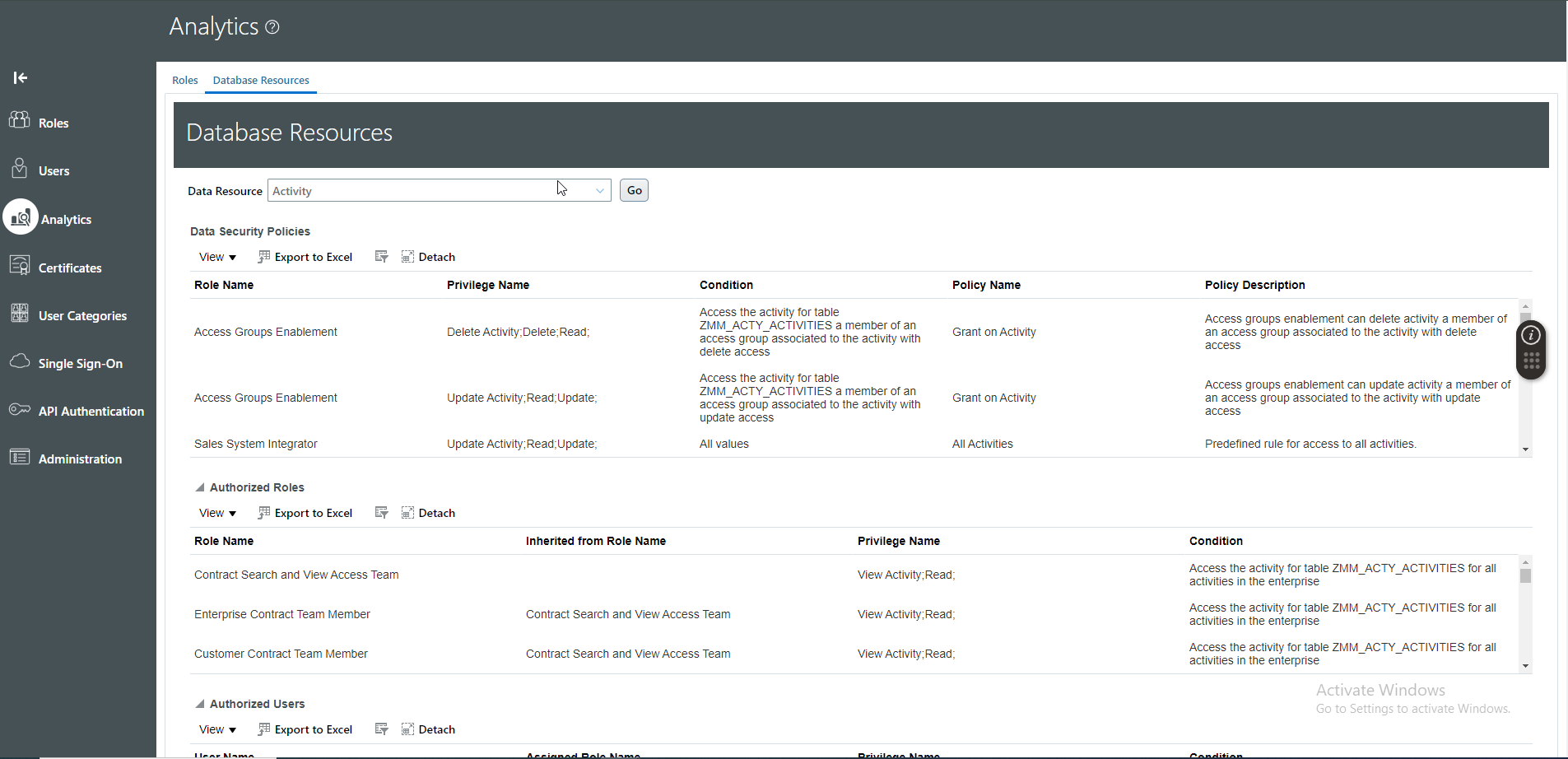
We can also view data security policies, and users associated with each database resource********.
(4) Certificates:
This section is used to Generate, export, or import PGP or X.509 certificates, which establish encryption keys for data exchanged between Oracle Cloud applications and other applications.
We will see encryption and decryption in more details in coming sections.
(5) User Categories:
We can segregate users based on user categories. Typical scenarios in which you want to group users are:
(5.1) Users belong to different organizations within an enterprise and each organization follows a different user management policy.
(5.2) Practices related to resetting passwords are not uniform across users
(5.3) Users have different preferences in receiving automated notifications for various tasks they perform in the application.
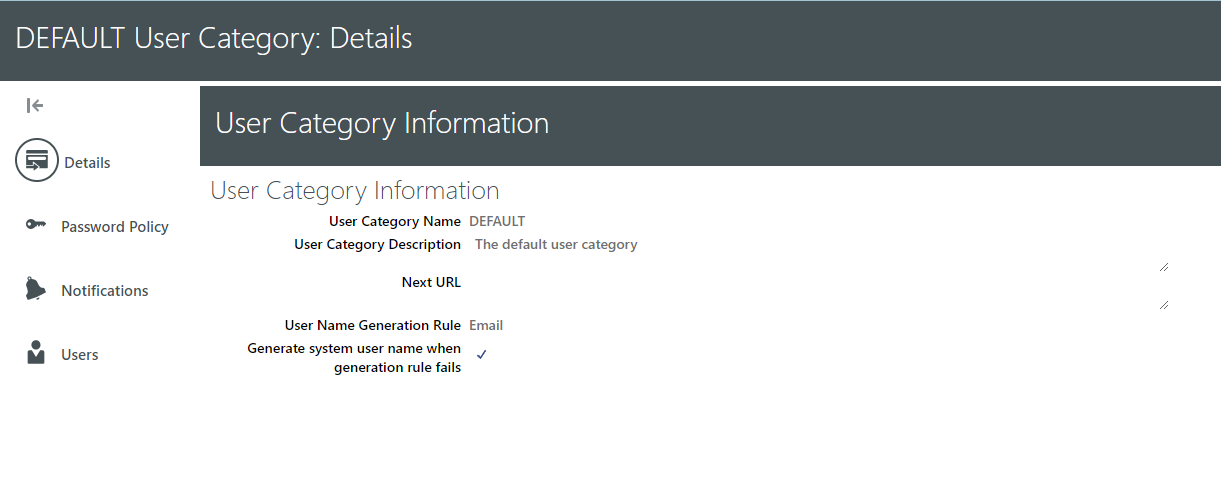
(A) Details: We have one DEFAULT user categories as default category for all users
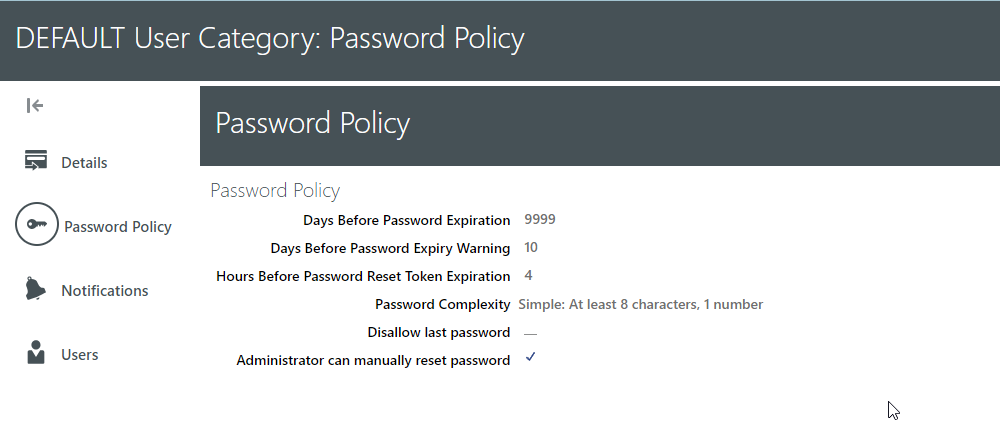
(B) Password Policy: We can define password policy which will set rules or conditions.
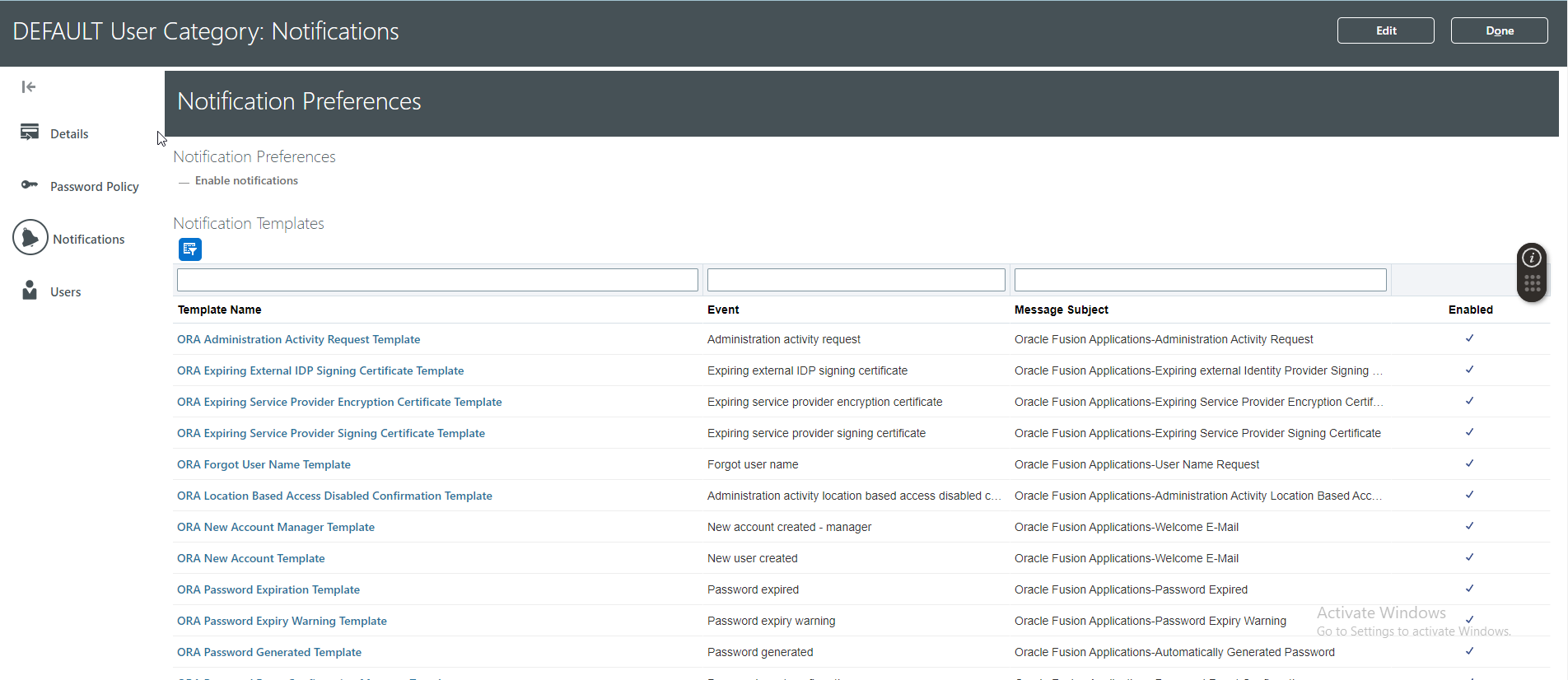
(C ) Notifications: Notifications are enabled by default, but you can disable them if required.We can enable or disable notifications separately for each user category.
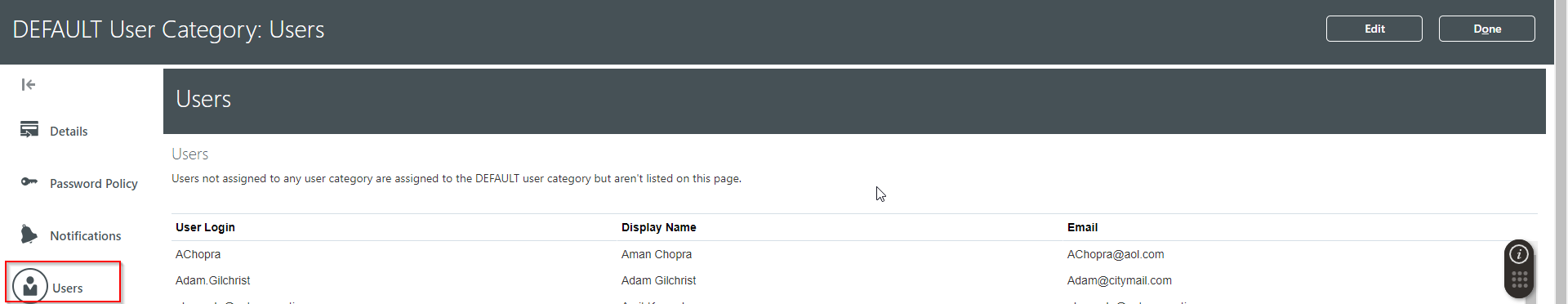
(D) Users: This section is used to add users to the user category.
(6) Single Sign-on: We will check single sign on in later section in details*****.
(7) API Authentication: We will check API Authentication in later section in details******
(8) Administration:
(8.1) Establish rules for the generation of usernames.
(8.2) Set password policies.
(8.3) Create standards for role definition, copying, and visualization.
(8.4) Review the status of role-copy operations.
(8.5) Define templates for notifications of user-account events, such as password expiration.
